Agents & Partners
NASDAQ is the world’s first computerized securities exchange.
NASDAQ mainly trades stocks of technology companies. Besides stock trading, NASDAQ also offers other financial services such as futures and derivatives trading, asset management, and data services.
The United States holds over 50% of the global stock market capitalization, gathering leading companies from various industries worldwide. NASDAQ accounts for over 50% of U.S. stock trading volume.
MDBS Digital is the only designated data integrator and interface provider for NASDAQ in Taiwan, offering clients the most stable and fastest U.S. stock market data and after-hours data services.
Agents & Partners
ICE owns and operates 12 regulated exchanges and markets including the ICE Futures exchanges in the U.S., Canada, and Europe, the European Liffe futures exchange, the New York Stock Exchange, the Options Exchange, and OTC energy, credit, and equity markets.
ICE Data Services provides market data and analytics across multiple asset classes to support investment, trading, compliance, and risk management. Solutions include real-time and historical data, indices, and trading information delivered securely and flexibly.
MDBS Digital supports ICE Data Services and API integration and offers large-scale customer service platform development.
Agents & Partners
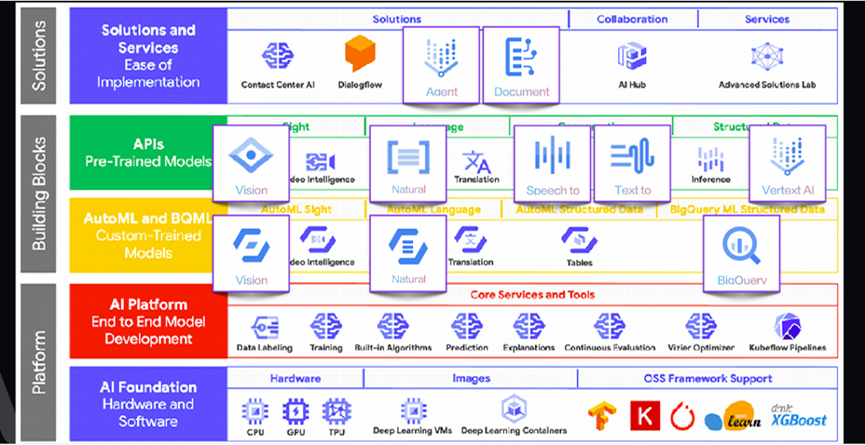
MDBS Digital provides AI system integration and innovative services in the Google environment, enhancing computing power interfaces and customized middleware.
They also support platforms including AI customer service, automatic video generation, research report production, and data integration, helping clients achieve effective connections between data and AI applications.
Agents & Partners
IBM collaborates with MDBS Digital to offer integrated securities and futures trading platforms, leveraging IBM mainframe high-performance computing to process large volumes of data and transactions while ensuring top-level security and reliability.
Mainframes play a critical role in business databases, trading servers, and applications requiring high flexibility and security, such as Linux on Power and Non-stop LinuxOne.
Additionally, they provide on-premise AI solutions to help highly regulated enterprises implement AI while safeguarding cybersecurity and personal data protection.
Agents & Partners

MT Newswires specializes in delivering global financial news, offering original, real-time, multi-asset news covering over 180 topics and reaching more than one billion readers.
MT Newswires’ news services are used by the world’s largest banks, brokerages, professional market data providers, financial portals, trading, wealth management, and research applications, renowned for its excellent service and real-time market insight.
MDBS Digital is the only designated data integrator and interface provider for MT Newswires in Taiwan, offering clients stable and fast U.S. stock and overseas commodities real-time news, target prices, and other data.
Agents & Partners
Interactive Brokers (IB) offers diverse financial product trading, including stocks, ETFs, futures, options, bonds, forex, funds, and CFDs, covering over 150 markets and 34 countries, with Chinese language interface and customer support.
MDBS Digital has partnered with IB to integrate enterprise asset management platforms and provides system integration services for domestic corporate users and institutional clients.

Security
Information Security Policy Statement
To ensure the thorough implementation, effective operation, supervision, and continuous improvement of our Information Security Management System (ISMS), and to safeguard the confidentiality, integrity, and availability of our company’s critical information systems, we hereby establish this Information Security Management Policy.
This policy serves as a clear guideline for all employees in their daily work. Every staff member is obligated to actively participate in the promotion and implementation of the policy to ensure the secure and stable operation of our personnel, data, information systems, equipment, and networks. We expect all staff to understand, implement, and maintain the policy to achieve the goal of uninterrupted information operations. For detailed regulations on using general IT equipment and network services, please refer to “ISMS-W-001: General IT Equipment Security Management Procedures.”
1. Enforce Information Security to Enhance Service Quality
All employees are responsible for implementing the ISMS. All information-related measures must ensure the confidentiality, integrity, and availability of business data. This includes protecting against external threats and improper internal management that may lead to data breaches, damage, or loss. Appropriate security measures must be selected to reduce risk to an acceptable level. Continuous monitoring, review, and auditing of the information security system will help improve service quality and raise service standards.
2. Strengthen Training to Ensure Continuous Operations
We supervise all staff in fulfilling information security responsibilities. Ongoing and appropriate security training is conducted annually to instill the concept that “Information security is everyone’s responsibility.” This raises awareness of the importance of information security and ensures compliance with related policies. The goal is to enhance awareness, response capability, and reduce security risks to support continuous business operations.
3. Establish Emergency Response and Swift Disaster Recovery
Emergency response and disaster recovery plans are created for critical information assets and key business functions. Regular drills of emergency response procedures are conducted to ensure rapid recovery in case of system failure or major incidents. This ensures the continuity of essential operations and minimizes potential losses.
4. Proper Use of Personal Data and Prevention of Data Breaches
Encryption and secure measures are used for the transmission and sharing of personal data. Regular evaluations of contractors’ compliance are conducted, and agreements are signed to ensure data security. Staff training is reinforced to increase awareness of data protection. Monitoring and review mechanisms are established to oversee the use, access, and transmission of personal data, and to detect and respond to any abnormal activities or security events in a timely manner. Personal data is securely and permanently deleted when no longer needed.